Connecting Through AWS VPC Peering
On This Page
Hevo provides you with the option of connecting to your AWS Source or Destination database, such as Amazon RDS or Amazon Aurora, via VPC peering. This option is available only under a business plan.
Note: The AWS database that you are connecting to must not be publicly accessible; it must not have a public IP address.
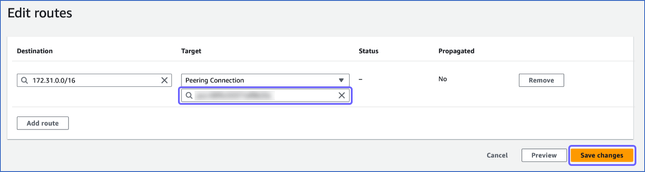
As seen in the image below, to establish a connection through VPC peering between the Hevo platform and your database, Hevo:

-
Creates an intermediate VPC or uses an existing one.
-
Peers an intermediate VPC with the VPC in which your database is created.
-
Communicates with your database through a tunnel instance inside the intermediate VPC.
The following image illustrates the steps for connecting your Source or Destination database through AWS VPC peering. The steps are also described in detail in the sections below.
Initiate VPC Peering Connection Request
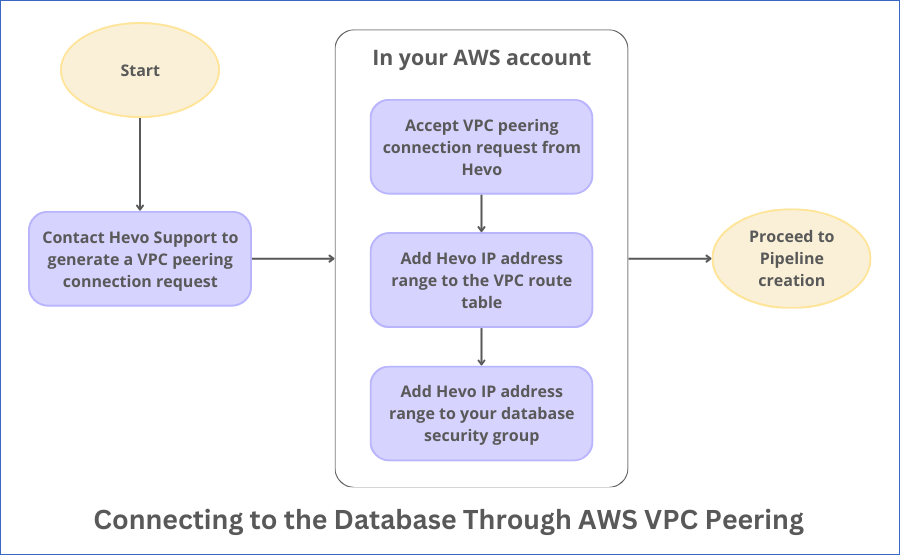
To create a VPC peering connection between your VPC (Accepter VPC) and Hevo’s VPC (Requester VPC), you must contact Hevo Support with the following details obtained from your AWS account:
-
AWS Account ID: The ID of the AWS account containing the VPC to be peered.
-
Accepter Classless Inter-Domain Routing (CIDR): The IP address range of your network in CIDR format. For example, 10.0.0.0/24.
-
Region: The AWS region of the account that hosts your Source or Destination database.
-
VPC ID: The ID of the VPC in which your Source or Destination database resides.
Based on these details, Hevo Support generates a VPC peering connection request and provides you with the following information:
-
Requester Classless Inter-Domain Routing (CIDR): The IP address range of Hevo’s network in CIDR format. For example, 10.0.0.0/28. You must add this IP address range to your VPC route table and database security group. Refer to the respective sections below.
-
Peering Connection ID: The ID of the peering connection request that Hevo generates. For example, pcx-011221a11abcd1011. You can use this to identify the peering connection request from Hevo.
Accept the VPC Peering Connection Request
-
Log in to your Amazon VPC console.
-
At the top right corner of the page, click the region selector to select your region from the drop-down. For example, Asia Pacific (Singapore).

-
In the left navigation pane, under Virtual private cloud, click Peering connections.

-
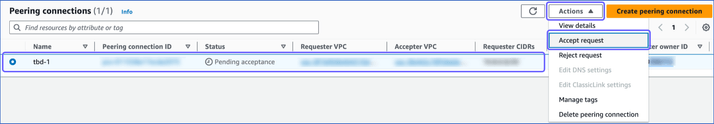
On the Peering connections page, do the following:
-
Click the Peering connection ID obtained in Step 1 above, click Actions, and select Accept request from the drop-down.
-
In the pop-up dialog that appears, click Accept request.

-
Add Hevo IP Address Range to your VPC Route Table
To direct the network traffic to Hevo’s IP address range through the VPC peering connection, add the range to your VPC route table. For this, perform the following steps:
Note: A VPC route table contains rules that define the path for communication inside the VPC.
-
Log in to your Amazon VPC console.
-
In the navigation pane, under Virtual private cloud, click Route tables.

-
On the Route tables page, click the Route table ID associated with your database VPC.
-
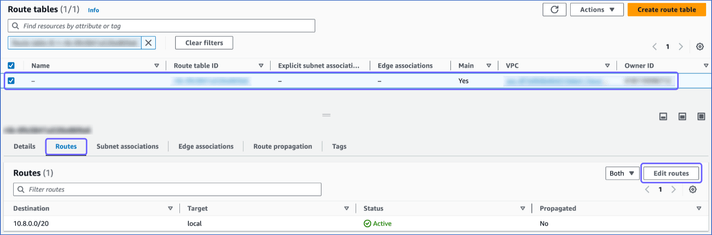
In the <Your Route table ID> description section, click Routes and then, click Edit routes.
-
On the Edit routes page, do the following:
Add Hevo IP Address Range to your Database Security Group
To allow inbound traffic to your database instance from Hevo, add Hevo’s IP address range to your database’s security group. For this, perform the following steps:
Note: A database security group contains rules for allowing access to the database from specific IP addresses or a range.
-
Log in to your Amazon VPC console.
-
In the left navigation pane, under Security, click Security groups.
-
On the Security Groups page, select the check box next to the Security group ID associated with your database and click Actions.
-
From the Actions drop-down, select Edit inbound rules.
-
On the Edit inbound rules page, do the following:

-
Click Add rule.
-
In the Type column, select the type of your database instance from the drop-down. For example, MYSQL/Aurora.
-
The Port range column is pre-filled with the port number of your database instance. For example, 3306 for a MySQL/Aurora database.
Note: This column is non-editable.
-
In the Source column, select Custom from the drop-down and enter Hevo’s IP address range obtained in Step 1 above.
-
Click Save rules.
-
Once you perform the steps above, you can configure your AWS database as a Source or Destination in Hevo.
Revision History
Refer to the following table for the list of key updates made to this page:
| Date | Release | Description of Change |
|---|---|---|
| Mar-21-2025 | NA | Added a note to clarify database accessibility to connect through VPC Peering. |
| Mar-25-2024 | 2.21.3 | New document. |