Connecting Through AWS VPC Endpoint
On This Page
An AWS VPC endpoint connection is feasible only when the Hevo region in which you want to create the Pipeline is the same as the AWS region of your Source or Destination.
Hevo provides you with the option of connecting to your Source or Destination database on AWS, such as Amazon RDS or Amazon Aurora, via an AWS VPC endpoint. This option is available only under a business plan.
As seen in the image below, to establish a connection between the Hevo platform and your database through an AWS private link using VPC endpoint services, Hevo:
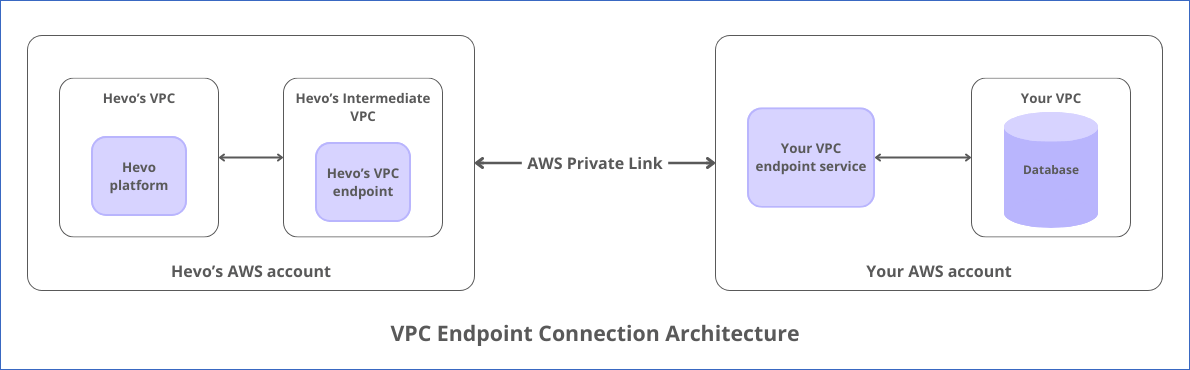
-
Creates an intermediate VPC or uses an existing one.
-
Creates an endpoint in the intermediate VPC to connect to your VPC endpoint service.
-
Communicates with your database through your VPC endpoint service, routing the network traffic via the AWS private link.
The following image illustrates the steps for connecting your Source or Destination database using an AWS VPC endpoint. The steps are also described in detail in the sections below.

Initiate VPC Endpoint Connection Request
To create an endpoint in Hevo’s VPC for connecting to your VPC endpoint service, you must contact Hevo Support with the following details obtained from your AWS account:
-
Endpoint Service name: The name assigned to the VPC endpoint service created for your database instance. For example, com.amazonaws.vpce.us-east-1.vpce-svc-0ab1abc2ae1c12345a.
-
Availability Zone (AZ): The location within your AWS region where the endpoint service is created. For example, us-east-1a in the AWS region, us-east-1.
-
Port: The port number on which your endpoint service listens for connections. For example, 3306 for MySQL (Aurora or RDS) databases.
On receiving these details, Hevo Support provides you with Hevo’s AWS account ID (AWS principal) or Amazon Resource Name (ARN). For example, arn:aws:iam::112233445566:root, where 112233445566 is the AWS account ID. You need to add this ARN as an allowed principal in your VPC endpoint service and inform the Support team about it.
The Support team then creates a VPC endpoint and provides you with the following information:
-
Domain Name System (DNS) Name: The name assigned by AWS to the VPC endpoint created by Hevo. For example, vpce-01e415dzazcc27acd-jq0m02b5.vpce-svc-0ab1abc2ae1c12345a.us-east-1.vpce.amazonaws.com. You must specify the DNS name as the database host while configuring your Source or Destination in Hevo.
-
Classless Inter-Domain Routing (CIDR) Range: The IP address range of Hevo’s network in CIDR format. For example, 10.0.0.0/28. You must add this IP address range to your database security group.
Accept the VPC Endpoint Connection Request
-
Log in to your Amazon VPC console.
-
At the top right corner of the page, click the region selector to select your region from the drop-down. For example, Asia Pacific (Singapore).

-
In the left navigation pane, under Virtual private cloud, click Endpoint services.
-
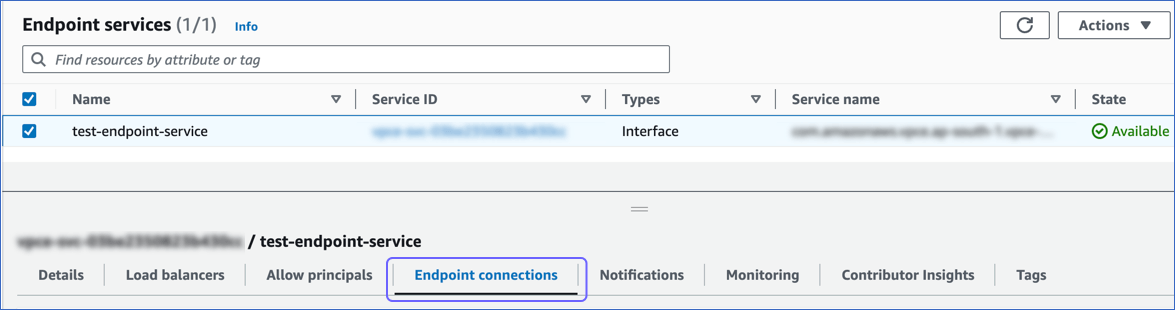
On the Endpoint services page, do the following:
-
Select the check box next to the Service ID of your VPC endpoint service and then click Endpoint connections.
-
In the Endpoint Connections panel, click the Endpoint ID whose Owner matches the account ID in the ARN obtained in Step 1 above. For example, if the ARN is arn:aws:iam::112233445566:root, the Endpoint ID is the one whose Owner is 112233445566.
-
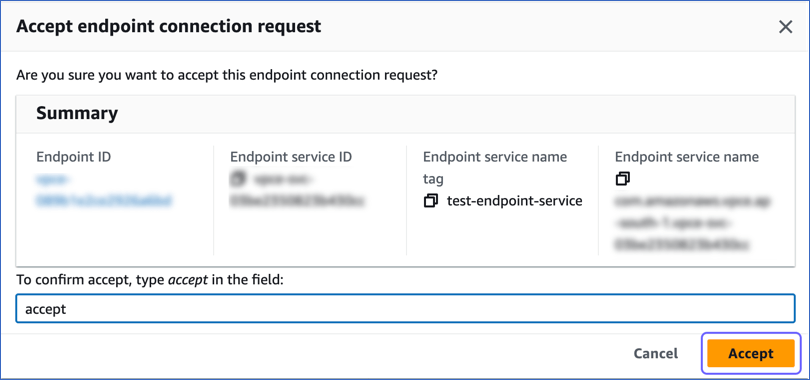
Click Actions, and from the drop-down, select Accept endpoint connection request.

-
In the pop-up dialog that appears, enter accept in the confirmation box and click Accept.
-
Grant the ARN access to your VPC Endpoint Service
To direct network traffic from Hevo to the database via your VPC endpoint service, you must allow the ARN received in Step 1 to connect to your endpoint service. For this, perform the following steps:
-
Log in to your Amazon VPC console.
-
In the navigation pane, under Virtual private cloud, click Endpoint services.

-
On the Endpoint services page, select the check box next to the Service ID of your VPC endpoint service and select the Allow principals tab.
-
In the panel that appears, click Allow principals.

-
On the page that opens, do the following:
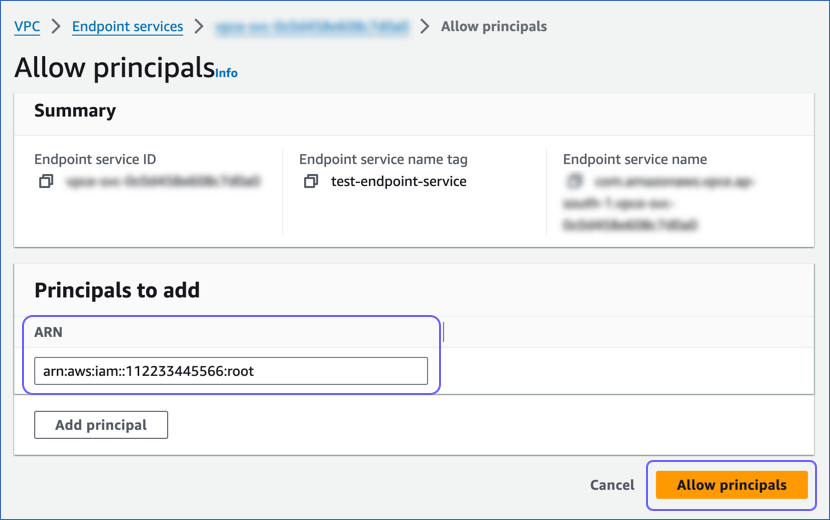
-
In the Principals to add section, specify the ARN in the following format: arn:aws:iam::<account_ID>:root. Replace the placeholder value with the AWS account ID obtained in Step 1 above. If you need to specify additional ARNs, click Add principal.
-
Click Allow principals.
-
Add Hevo IP Address Range to your Database Security Group
To allow inbound traffic to your database instance from Hevo, add Hevo’s IP address range to your database’s security group. For this, perform the following steps:
-
Log in to your Amazon VPC console.
-
In the left navigation pane, under Security, click Security groups.
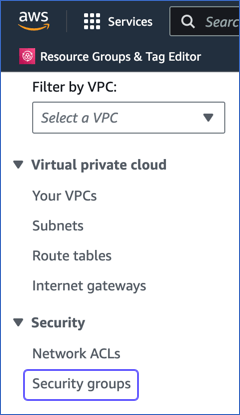
-
On the Security Groups page, select the check box next to the Security group ID associated with your database and click Actions.
-
From the Actions drop-down, select Edit inbound rules.
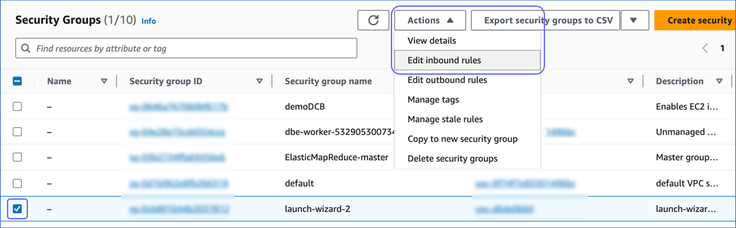
-
On the Edit inbound rules page, do the following:

-
Click Add rule.
-
In the Type column, select the type of your database instance from the drop-down. For example, MYSQL/Aurora.
-
The Port range column is pre-filled with the port number of your database instance. For example, 3306 for a MySQL/Aurora database.
Note: This column is non-editable.
-
In the Source column, select Custom from the drop-down and enter Hevo’s IP address range obtained in Step 1 above.
-
Click Save rules.
-
Once you perform the steps above, you can configure your database as a Source or Destination in Hevo. You need to specify the DNS name obtained in Step 1 as your Database Host.
Revision History
Refer to the following table for the list of key updates made to this page:
| Date | Release | Description of Change |
|---|---|---|
| Sep-02-2024 | NA | - Added a banner at the top to emphasize that the VPCs should be in the same region. - Reorganized the content in Initiate VPC Endpoint Connection Request for clarity. |
| Apr-15-2024 | 2.22.2 | New document. |