Activity Logs - CloudWatch Sync
On This Page
Amazon CloudWatch Logs is a monitoring and management service provided by Amazon Web Services (AWS). It allows you to collect and track metrics, collect and monitor log files, and set alarms.
You can push the activity logs corresponding to actions, status updates, and failures for any Hevo assets, such as Pipelines, Models, and Workflows, to your CloudWatch Logs account.
Note: Starting Release 2.17, the Workflows feature and its activity logs are available only for existing users. Users signing up from Release 2.17 onwards cannot create Workflows. For more information, please contact Hevo Support or your account executive.
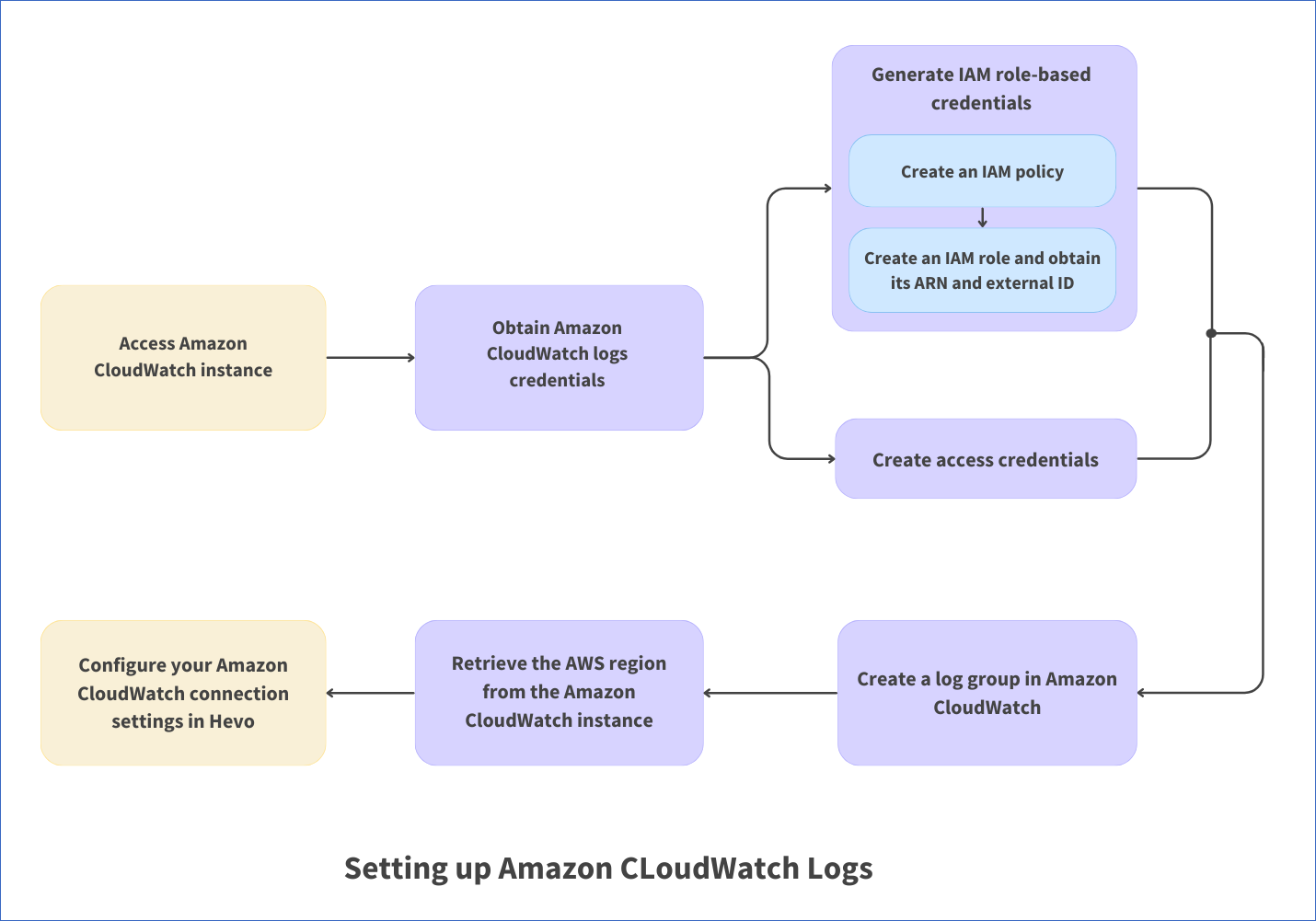
The following image illustrates the key steps that you need to complete to configure Amazon CloudWatch Logs in Hevo:
Prerequisites
-
An active Amazon Web Services (AWS) account is available.
-
If you are logged in as an IAM user, you have permission to:
-
Create the access credentials or generate IAM role-based credentials.
-
Obtain or create the IAM policies.
-
-
A valid access key and secret access key is available in AWS.
Obtain Amazon CloudWatch Logs Credentials
You must either Create access credentials or Generate IAM role-based credentials to allow Hevo to connect to your Amazon CloudWatch account and sync logs with it.
Create access credentials
You need the access key and secret access key from your Amazon CloudWatch account to allow Hevo to access the data from it.
-
Log in to the Amazon IAM Console.
-
In the left navigation bar, under Access management, click Users, and then, in the right pane, click the User name for which you want to create an access key.

-
In the Summary page, click the Security credentials tab, and then, click Create access key.

-
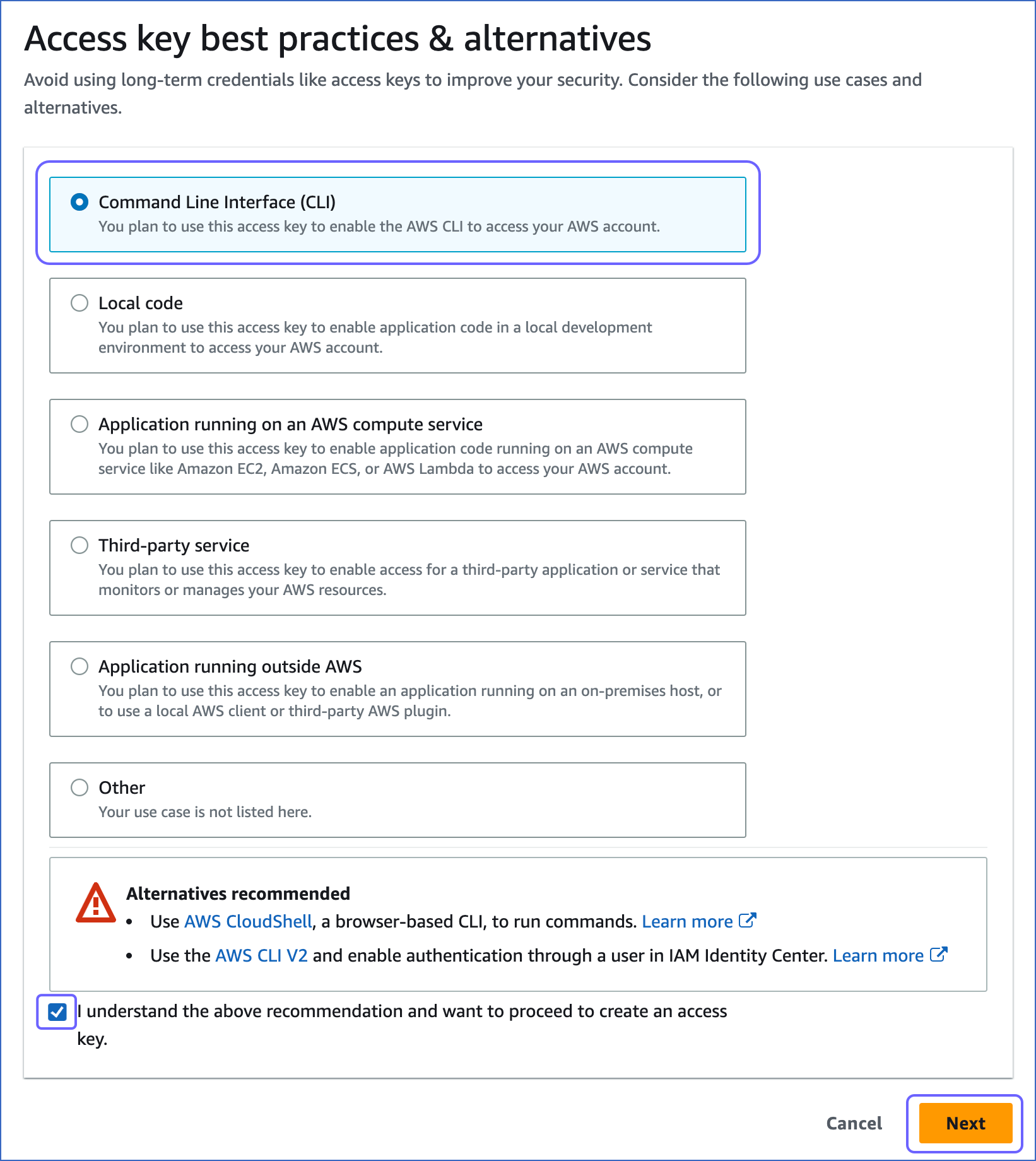
In the Access key best practices & alternatives page, do the following:
-
Select one of the recommended methods. For example, in the image above, Command Line Interface (CLI) is selected.
-
Select the I understand the above recommendation… check box, to proceed with creating the access key.
-
Click Next.
-
-
In the Set description tag - optional page, do the following:

-
(Optional) Specify a description for the access key in the Description tag value field.
-
Click Create access key.
-
-
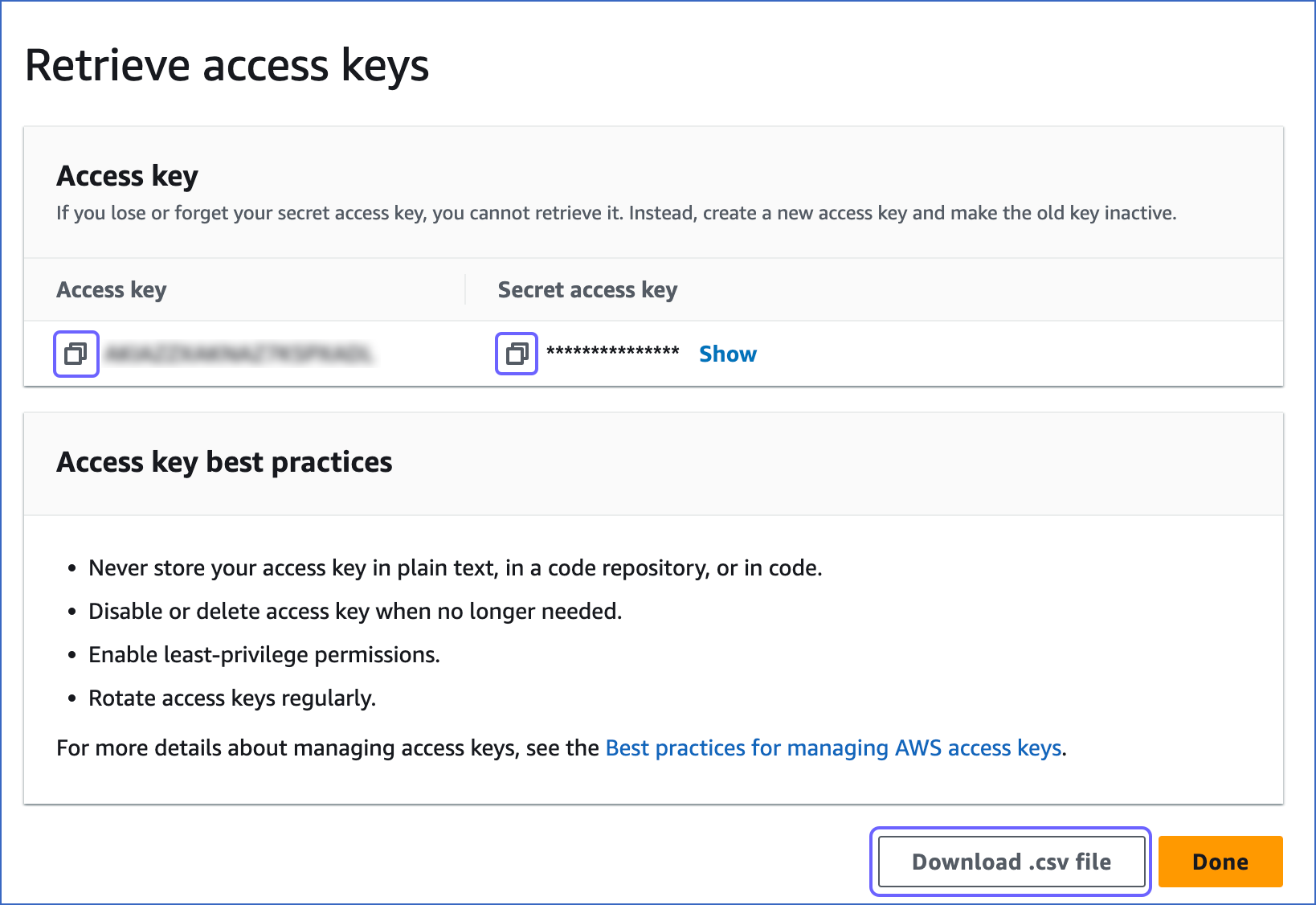
In the Retrieve access keys page, do the following:
-
Click the copy icon in the Access key field and save the key securely like any other password.
-
Click the copy icon in the Secret access key field and save the key securely like any other password.
Note: Once you exit this page, you cannot access these keys again.
-
(Optional) Click Download .csv file to save the access key and the secret access key on your local machine.
-
Generate IAM role-based credentials
To generate your IAM role-based credentials, you need to:
-
Create an IAM policy with the permission to allow Hevo to sync data with your Amazon CloudWatch logs.
-
Create an IAM role for Hevo, as the Amazon Resource Name (ARN) and the external ID from this role are required to configure Amazon CloudWatch Logs in Hevo.
These steps are explained in details below:
1. Create an IAM policy
-
Log in to the AWS IAM Console.
-
In the left navigation bar, under Access management, click Policies.

-
In the Policies page, click Create policy.

-
In the Specify permissions page, click the JSON tab and paste the following policy in the editor. The JSON statements list the permissions the policy would assign to Hevo.
Note: Replace the placeholder values in the commands below with your own. For example, <aws_region> with us-east-1.
{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": "logs:CreateLogStream", "Resource": "arn:aws:logs:<aws_region>:<account-id>:log-group:<log-group-name>" }, { "Sid": "VisualEditor1", "Effect": "Allow", "Action": [ "logs:DeleteLogStream", "logs:PutLogEvents" ], "Resource": "arn:aws:logs:<aws_region>:<account-id>:log-group:<log-group-name>" } ] }
-
Click Next.
-
In the Review and policy page, specify a Policy name and Description for your policy and click Create policy.
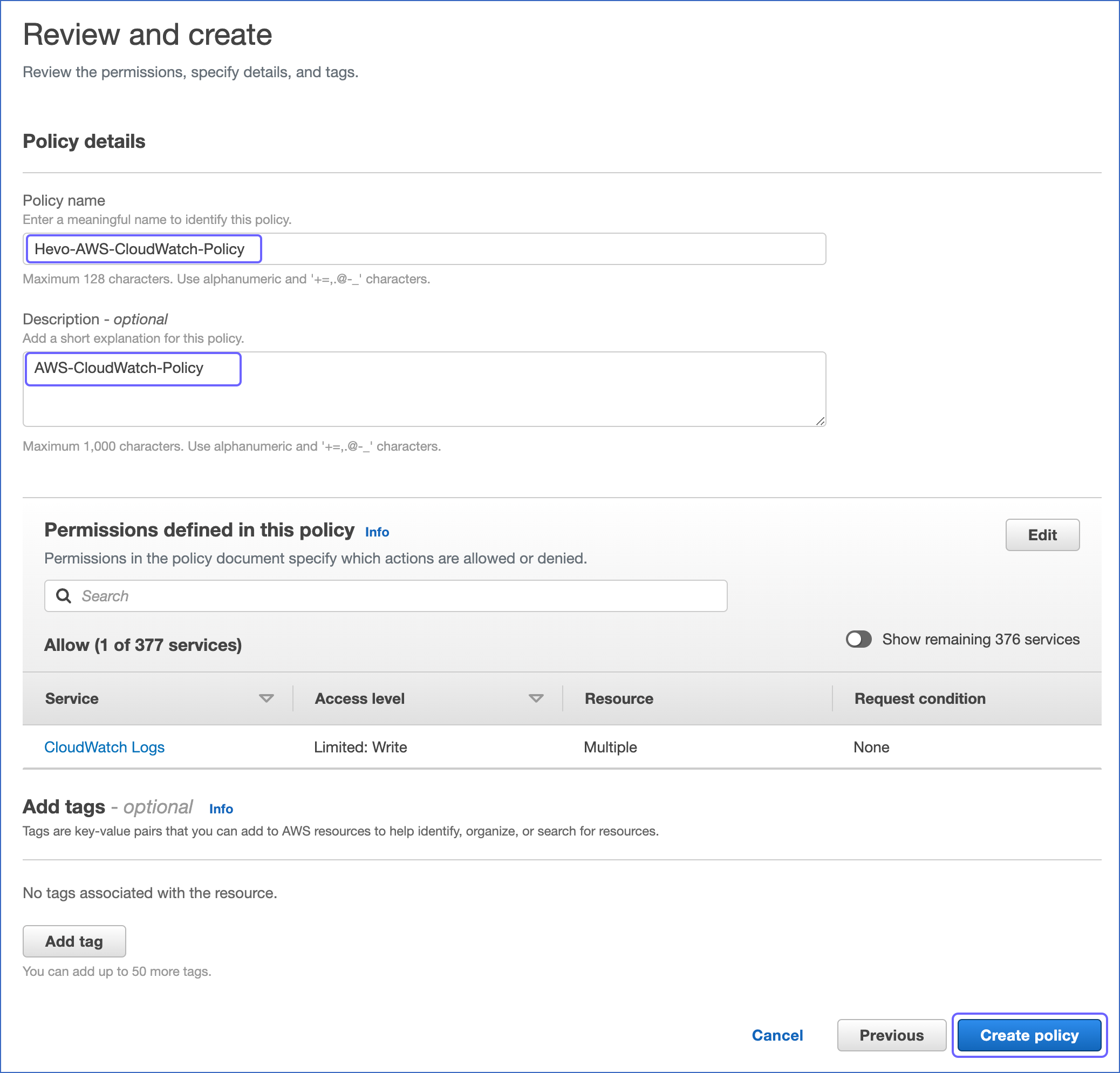
You are redirected to the Policies page, where you can see the policy that you created.
2. Create an IAM role and obtain its ARN and external ID
Perform the following steps to create an IAM role:
-
Log in to the AWS IAM Console.
-
In the left navigation bar, under Access management, click Roles.

-
In the Roles page, click Create role.

-
In the Select trusted entity page:
-
In the Trusted entity type section, select AWS account.

-
In the An AWS account section, do the following:

-
Select the Another AWS account option, and specify Hevo’s Account ID, 393309748692.
-
In the Options section, select the Require external ID… check box, and specify an External ID of your choice.
Note: You must save this external ID in a secure location like any other password. This is required while setting up a Pipeline in Hevo.
-
-
-
Click Next.
-
In the Permissions policies section, select the policy that you created in Create an IAM policy above and click Next at the bottom of the page.
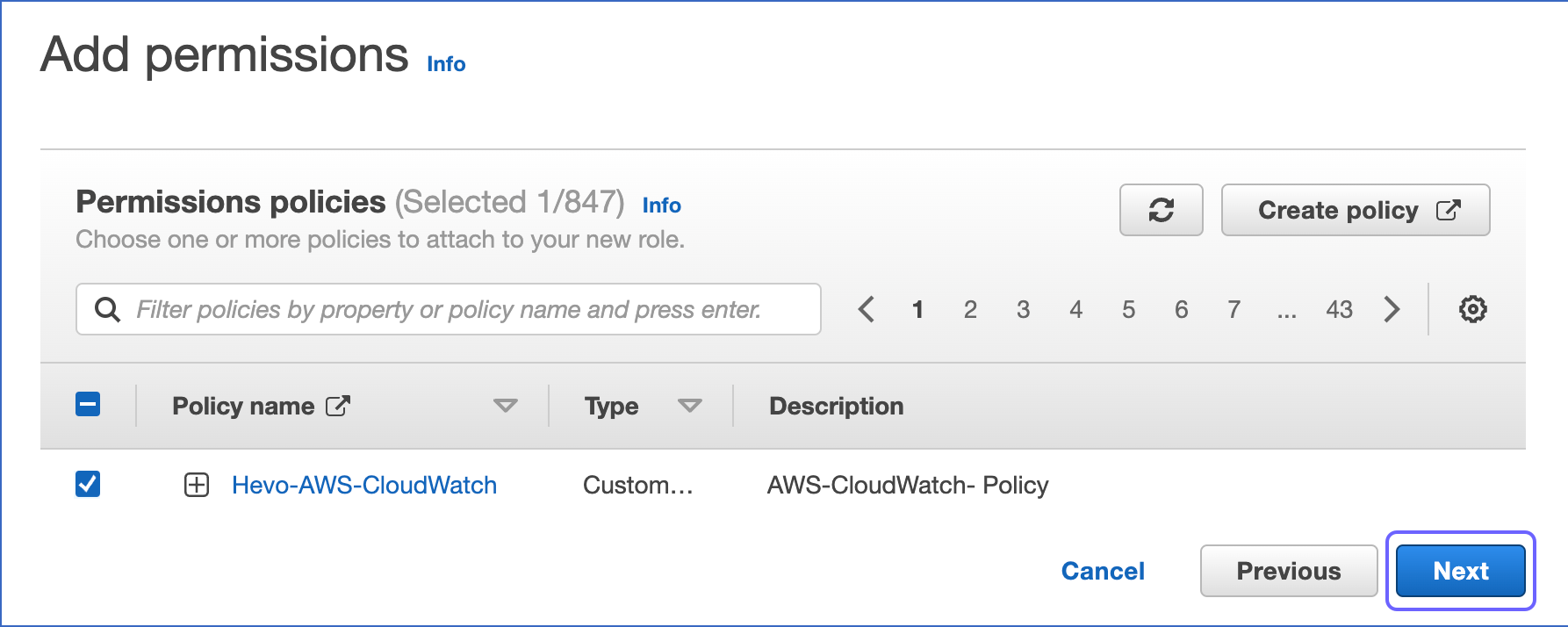
-
In the Name, review, and create page, specify the Role name and click Create role.
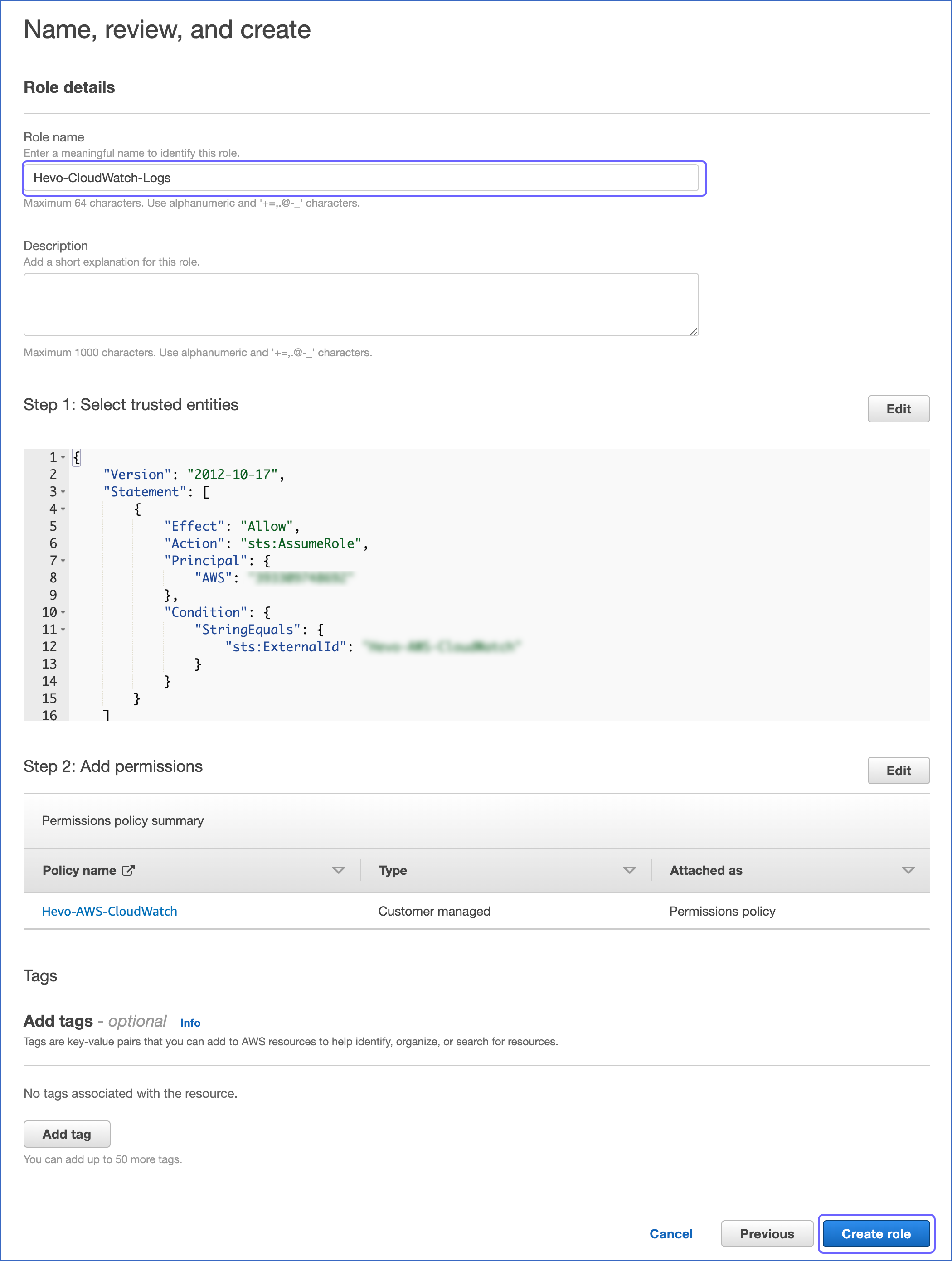
-
In the Roles page, select the role that you created above.

-
In the <Role name> page, the Summary section, click the copy icon to copy the ARN and save it securely like any other password. Use this ARN while configuring Amazon CloudWatch logs in Hevo.

Create a Log Group for Amazon CloudWatch
-
Log in to the AWS CloudWatch Console.
-
In the left navigation bar, under Logs, click Log groups.
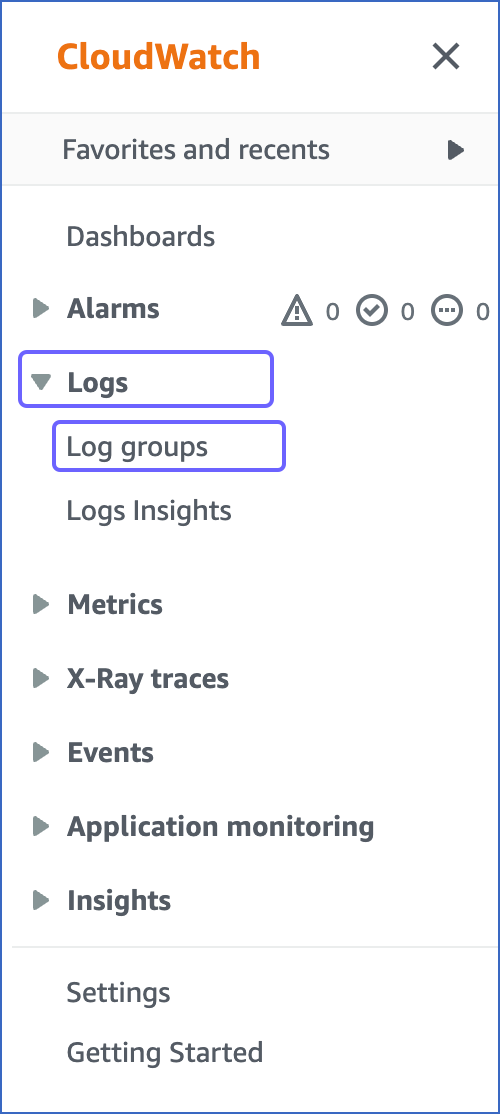
-
In the Log groups page, click Create log group.

-
In the Create log group page, specify the following:
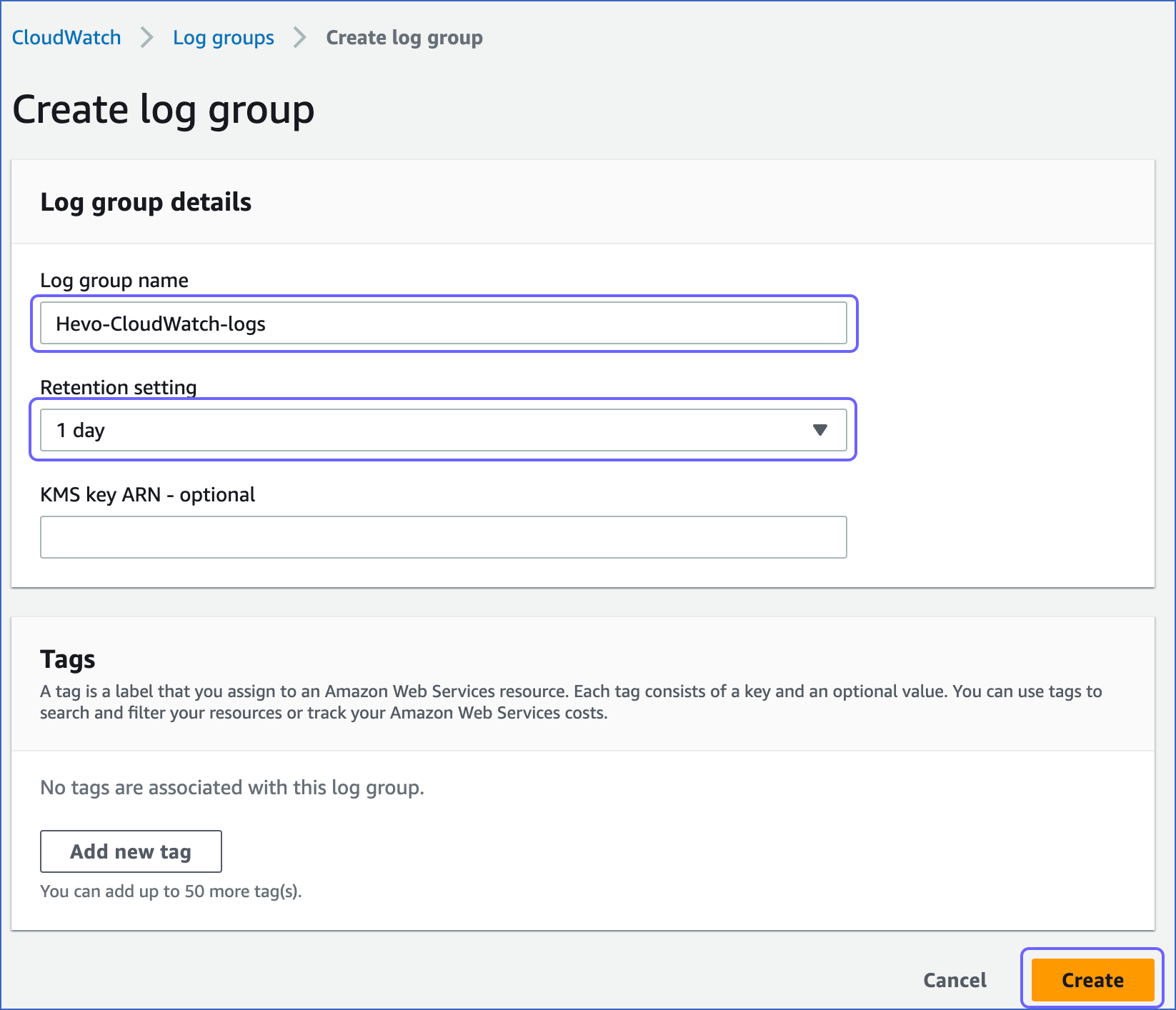
-
Log group name: A unique name for your log.
-
Retention setting: The duration for which your organization wants to retain information.
-
Click Create.
-
-
In the Log groups page, click the log group that you created above.

-
In the Log group details section, copy the ARN and save it securely like any other password. Use this ARN while configuring your Amazon CloudWatch Logs in Hevo.

Retrieve the AWS Region
To configure Amazon CloudWatch in Hevo you need to provide the AWS region where your logs are available.
To retrieve your AWS region:
-
Log in to the Amazon CloudWatch Console, and in the top-right corner of the page, locate the AWS region.

Configure your Amazon CloudWatch Settings
Perform the following steps to configure Amazon CloudWatch:
-
Log in to your Hevo account.
-
In the User Information Panel, click the drop-down next to your username and click Team.

-
In the left navigation bar, click Activity Logs and click ENABLE, to enable CloudWatch Sync for your activity logs.

-
In the CloudWatch Sync Settings window, select one of the methods to sync your activity logs to your CloudWatch Logs account:
-
Connect using IAM Role:

-
IAM Role ARN: The Amazon Resource Name (ARN) for your Amazon CloudWatch that you retrieved above.
-
External Id: The external ID that you specified above.
-
Region: The AWS region where your CloudWatch log group is created.
-
Log Group: The log group that you created in Step 2.
-
-
Connect using Access Credentials:

-
AWS Key: The AWS access key that you retrieved in the Create access credentials section above.
-
AWS Secret: The AWS secret access key for the access key ID that you retrieved in the Create access credentials section above.
-
Region: The AWS region where your CloudWatch log group is created.
-
Log Group: The log group that you created in Step 3.
-
-
-
Click TEST CONNECTION to check connectivity with your Amazon CloudWatch Logs account and click ENABLE.
Revision History
Refer to the following table for the list of key updates made to this page:
| Date | Release | Description of Change |
|---|---|---|
| Apr-25-2023 | 2.12 | Added sections: - Obtain Amazon CloudWatch Logs Credentials - Create a Log Group for Amazon CloudWatch. |