- Introduction
- Getting Started
- Creating an Account in Hevo
- Subscribing to Hevo via AWS Marketplace
- Connection Options
- Familiarizing with the UI
- Creating your First Pipeline
- Data Loss Prevention and Recovery
- Data Ingestion
- Data Loading
- Loading Data in a Database Destination
- Loading Data to a Data Warehouse
- Optimizing Data Loading for a Destination Warehouse
- Deduplicating Data in a Data Warehouse Destination
- Manually Triggering the Loading of Events
- Scheduling Data Load for a Destination
- Loading Events in Batches
- Data Loading Statuses
- Data Spike Alerts
- Name Sanitization
- Table and Column Name Compression
- Parsing Nested JSON Fields in Events
- Pipelines
- Data Flow in a Pipeline
- Familiarizing with the Pipelines UI
- Working with Pipelines
- Managing Objects in Pipelines
- Pipeline Jobs
-
Transformations
-
Python Code-Based Transformations
- Supported Python Modules and Functions
-
Transformation Methods in the Event Class
- Create an Event
- Retrieve the Event Name
- Rename an Event
- Retrieve the Properties of an Event
- Modify the Properties for an Event
- Fetch the Primary Keys of an Event
- Modify the Primary Keys of an Event
- Fetch the Data Type of a Field
- Check if the Field is a String
- Check if the Field is a Number
- Check if the Field is Boolean
- Check if the Field is a Date
- Check if the Field is a Time Value
- Check if the Field is a Timestamp
-
TimeUtils
- Convert Date String to Required Format
- Convert Date to Required Format
- Convert Datetime String to Required Format
- Convert Epoch Time to a Date
- Convert Epoch Time to a Datetime
- Convert Epoch to Required Format
- Convert Epoch to a Time
- Get Time Difference
- Parse Date String to Date
- Parse Date String to Datetime Format
- Parse Date String to Time
- Utils
- Examples of Python Code-based Transformations
-
Drag and Drop Transformations
- Special Keywords
-
Transformation Blocks and Properties
- Add a Field
- Change Datetime Field Values
- Change Field Values
- Drop Events
- Drop Fields
- Find & Replace
- Flatten JSON
- Format Date to String
- Format Number to String
- Hash Fields
- If-Else
- Mask Fields
- Modify Text Casing
- Parse Date from String
- Parse JSON from String
- Parse Number from String
- Rename Events
- Rename Fields
- Round-off Decimal Fields
- Split Fields
- Examples of Drag and Drop Transformations
- Effect of Transformations on the Destination Table Structure
- Transformation Reference
- Transformation FAQs
-
Python Code-Based Transformations
-
Schema Mapper
- Using Schema Mapper
- Mapping Statuses
- Auto Mapping Event Types
- Manually Mapping Event Types
- Modifying Schema Mapping for Event Types
- Schema Mapper Actions
- Fixing Unmapped Fields
- Resolving Incompatible Schema Mappings
- Resizing String Columns in the Destination
- Schema Mapper Compatibility Table
- Limits on the Number of Destination Columns
- File Log
- Troubleshooting Failed Events in a Pipeline
- Mismatch in Events Count in Source and Destination
- Audit Tables
- Activity Log
-
Pipeline FAQs
- Can multiple Sources connect to one Destination?
- What happens if I re-create a deleted Pipeline?
- Why is there a delay in my Pipeline?
- Can I change the Destination post-Pipeline creation?
- Why is my billable Events high with Delta Timestamp mode?
- Can I drop multiple Destination tables in a Pipeline at once?
- How does Run Now affect scheduled ingestion frequency?
- Will pausing some objects increase the ingestion speed?
- Can I see the historical load progress?
- Why is my Historical Load Progress still at 0%?
- Why is historical data not getting ingested?
- How do I set a field as a primary key?
- How do I ensure that records are loaded only once?
- Events Usage
- Sources
- Free Sources
-
Databases and File Systems
- Data Warehouses
-
Databases
- Connecting to a Local Database
- Amazon DocumentDB
- Amazon DynamoDB
- Elasticsearch
-
MongoDB
- Generic MongoDB
- MongoDB Atlas
- Support for Multiple Data Types for the _id Field
- Example - Merge Collections Feature
-
Troubleshooting MongoDB
-
Errors During Pipeline Creation
- Error 1001 - Incorrect credentials
- Error 1005 - Connection timeout
- Error 1006 - Invalid database hostname
- Error 1007 - SSH connection failed
- Error 1008 - Database unreachable
- Error 1011 - Insufficient access
- Error 1028 - Primary/Master host needed for OpLog
- Error 1029 - Version not supported for Change Streams
- SSL 1009 - SSL Connection Failure
- Troubleshooting MongoDB Change Streams Connection
- Troubleshooting MongoDB OpLog Connection
-
Errors During Pipeline Creation
- SQL Server
-
MySQL
- Amazon Aurora MySQL
- Amazon RDS MySQL
- Azure MySQL
- Generic MySQL
- Google Cloud MySQL
- MariaDB MySQL
-
Troubleshooting MySQL
-
Errors During Pipeline Creation
- Error 1003 - Connection to host failed
- Error 1006 - Connection to host failed
- Error 1007 - SSH connection failed
- Error 1011 - Access denied
- Error 1012 - Replication access denied
- Error 1017 - Connection to host failed
- Error 1026 - Failed to connect to database
- Error 1027 - Unsupported BinLog format
- Failed to determine binlog filename/position
- Schema 'xyz' is not tracked via bin logs
- Errors Post-Pipeline Creation
-
Errors During Pipeline Creation
- MySQL FAQs
- Oracle
-
PostgreSQL
- Amazon Aurora PostgreSQL
- Amazon RDS PostgreSQL
- Azure PostgreSQL
- Generic PostgreSQL
- Google Cloud PostgreSQL
- Heroku PostgreSQL
-
Troubleshooting PostgreSQL
-
Errors during Pipeline creation
- Error 1003 - Authentication failure
- Error 1006 - Connection settings errors
- Error 1011 - Access role issue for logical replication
- Error 1012 - Access role issue for logical replication
- Error 1014 - Database does not exist
- Error 1017 - Connection settings errors
- Error 1023 - No pg_hba.conf entry
- Error 1024 - Number of requested standby connections
- Errors Post-Pipeline Creation
-
Errors during Pipeline creation
- PostgreSQL FAQs
- Troubleshooting Database Sources
- File Storage
- Engineering Analytics
- Finance & Accounting Analytics
-
Marketing Analytics
- ActiveCampaign
- AdRoll
- Amazon Ads
- Apple Search Ads
- AppsFlyer
- CleverTap
- Criteo
- Drip
- Facebook Ads
- Facebook Page Insights
- Firebase Analytics
- Freshsales
- Google Ads
- Google Analytics
- Google Analytics 4
- Google Analytics 360
- Google Play Console
- Google Search Console
- HubSpot
- Instagram Business
- Klaviyo
- Lemlist
- LinkedIn Ads
- Mailchimp
- Mailshake
- Marketo
- Microsoft Ads
- Onfleet
- Outbrain
- Pardot
- Pinterest Ads
- Pipedrive
- Recharge
- Segment
- SendGrid Webhook
- SendGrid
- Salesforce Marketing Cloud
- Snapchat Ads
- SurveyMonkey
- Taboola
- TikTok Ads
- Twitter Ads
- Typeform
- YouTube Analytics
- Product Analytics
- Sales & Support Analytics
- Source FAQs
- Destinations
- Familiarizing with the Destinations UI
- Cloud Storage-Based
- Databases
-
Data Warehouses
- Amazon Redshift
- Azure Synapse Analytics
- Databricks
- Firebolt
- Google BigQuery
- Hevo Managed Google BigQuery
- Snowflake
-
Destination FAQs
- Can I change the primary key in my Destination table?
- How do I change the data type of table columns?
- Can I change the Destination table name after creating the Pipeline?
- How can I change or delete the Destination table prefix?
- Why does my Destination have deleted Source records?
- How do I filter deleted Events from the Destination?
- Does a data load regenerate deleted Hevo metadata columns?
- How do I filter out specific fields before loading data?
- Transform
- Alerts
- Account Management
- Activate
- Glossary
Releases- Release 2.22.2 (Apr 15-Apr 22, 2024)
- Release 2.22.1 (Apr 08-Apr 15, 2024)
- Release 2.22 (Mar 04-Apr 01, 2024)
- 2024 Releases
-
2023 Releases
- Release 2.19 (Dec 04, 2023-Jan 15, 2024)
- Release Version 2.18
- Release Version 2.17
- Release Version 2.16 (with breaking changes)
- Release Version 2.15 (with breaking changes)
- Release Version 2.14
- Release Version 2.13
- Release Version 2.12
- Release Version 2.11
- Release Version 2.10
- Release Version 2.09
- Release Version 2.08
- Release Version 2.07
- Release Version 2.06
-
2022 Releases
- Release Version 2.05
- Release Version 2.04
- Release Version 2.03
- Release Version 2.02
- Release Version 2.01
- Release Version 2.00
- Release Version 1.99
- Release Version 1.98
- Release Version 1.97
- Release Version 1.96
- Release Version 1.95
- Release Version 1.93 & 1.94
- Release Version 1.92
- Release Version 1.91
- Release Version 1.90
- Release Version 1.89
- Release Version 1.88
- Release Version 1.87
- Release Version 1.86
- Release Version 1.84 & 1.85
- Release Version 1.83
- Release Version 1.82
- Release Version 1.81
- Release Version 1.80 (Jan-24-2022)
- Release Version 1.79 (Jan-03-2022)
-
2021 Releases
- Release Version 1.78 (Dec-20-2021)
- Release Version 1.77 (Dec-06-2021)
- Release Version 1.76 (Nov-22-2021)
- Release Version 1.75 (Nov-09-2021)
- Release Version 1.74 (Oct-25-2021)
- Release Version 1.73 (Oct-04-2021)
- Release Version 1.72 (Sep-20-2021)
- Release Version 1.71 (Sep-09-2021)
- Release Version 1.70 (Aug-23-2021)
- Release Version 1.69 (Aug-09-2021)
- Release Version 1.68 (Jul-26-2021)
- Release Version 1.67 (Jul-12-2021)
- Release Version 1.66 (Jun-28-2021)
- Release Version 1.65 (Jun-14-2021)
- Release Version 1.64 (Jun-01-2021)
- Release Version 1.63 (May-19-2021)
- Release Version 1.62 (May-05-2021)
- Release Version 1.61 (Apr-20-2021)
- Release Version 1.60 (Apr-06-2021)
- Release Version 1.59 (Mar-23-2021)
- Release Version 1.58 (Mar-09-2021)
- Release Version 1.57 (Feb-22-2021)
- Release Version 1.56 (Feb-09-2021)
- Release Version 1.55 (Jan-25-2021)
- Release Version 1.54 (Jan-12-2021)
-
2020 Releases
- Release Version 1.53 (Dec-22-2020)
- Release Version 1.52 (Dec-03-2020)
- Release Version 1.51 (Nov-10-2020)
- Release Version 1.50 (Oct-19-2020)
- Release Version 1.49 (Sep-28-2020)
- Release Version 1.48 (Sep-01-2020)
- Release Version 1.47 (Aug-06-2020)
- Release Version 1.46 (Jul-21-2020)
- Release Version 1.45 (Jul-02-2020)
- Release Version 1.44 (Jun-11-2020)
- Release Version 1.43 (May-15-2020)
- Release Version 1.42 (Apr-30-2020)
- Release Version 1.41 (Apr-2020)
- Release Version 1.40 (Mar-2020)
- Release Version 1.39 (Feb-2020)
- Release Version 1.38 (Jan-2020)
- Early Access New
- Upcoming Features
Generic PostgreSQL
Starting Release 2.19, Hevo has stopped supporting XMIN as a query mode for all variants of the PostgreSQL Source. As a result, you will not be able to create new Pipelines using this query mode. This change does not affect existing Pipelines. However, you will not be able to change the query mode to XMIN for any objects currently ingesting data using other query modes.
PostgreSQL is a highly stable database management system, used as the primary data store or data warehouse for many web, mobile, geospatial, and analytics applications. Generic PostgreSQL represents a self-hosted PostgreSQL server.
You can ingest data from your PostgreSQL database using Hevo Pipelines and replicate it to a Destination of your choice.
Prerequisites
-
IP address or host name of your PostgreSQL server is available.
-
The PostgreSQL version is 9.5 or higher.
-
Log-based incremental replication is enabled if ingestion mode is Logical Replication.
-
SELECT, USAGE, and CONNECT privileges are granted to the database user.
Note: We recommend that you create a database user for configuring your PostgreSQL Source in Hevo. However, if you already have one, refer to section Grant privileges to the user.
-
You are assigned the Team Administrator, Team Collaborator, or Pipeline Administrator role in Hevo to create the Pipeline.
Perform the following steps to configure your Generic PostgreSQL Source:
Set up Log-based Incremental Replication
Hevo supports data ingestion replication from PostgreSQL servers via Write Ahead Logs (WALs) set at the logical level (available on PostgreSQL version 9.4 and above).
A WAL is a collection of log files that record information about data modifications and data object modifications made on a PostgreSQL server instance. Typically, WAL is used for data replication and data recovery.
To configure logical replication, enable WAL on the self-hosted (generic) PostgreSQL server:
1. Update the client authentication file
Modify the PostgreSQL configuration file, postgresql.conf, generally found in the /etc/postgresql/\<version\>/main/ directory in the Linux system.
| Parameter | Value | Description |
|---|---|---|
max_replication_slots |
Any whole number between 1 and 10 | The number of clients that can connect to the server. Default value: 10. |
max_wal_senders |
10 | The number of processes that can simultaneously transmit the WAL log. Default value: 10. |
wal_level |
logical | The amount of information being written to the WAL log. For example, minimal, replica, or logical. Default value: replica. The value logical is required to enable log-based replication. |
wal_sender_timeout |
0 | The time, in seconds, after which PostgreSQL terminates the replication connections due to inactivity. Default value: 60 seconds. You must set the value to 0 so that the connections are never terminated and your Pipeline does not fail. |
2. Update the PostgreSQL database configuration file
In the pg_hba.conf file, assign permission to the database user to connect from an external network to the PostgreSQL server:
local replication <user> peer
host replication <user> 127.0.0.1/0 md5
host replication <user> ::1/0 md5
Note: Remember to replace <user> with your intended user.
3. Enable access to WALs
Once you have successfully completed the above steps, do the following:
-
Restart the PostgreSQL server.
-
Provide access to the WAL for the database user:
alter role <user> with replication; alter role <user> with login;Note: Remember to replace <user> with your intended user.
Whitelist Hevo’s IP Addresses
You need to whitelist the Hevo IP addresses for your region to enable Hevo to connect to your PostgreSQL database. To do this:
-
Log in to the PostgreSQL server as a Superuser.
-
In the
postgresql.conffile, add the Hevo IP addresses for your region or add*for thelisten_addressesparameter to allow all IPs to connect. -
Navigate to the PostgreSQL configuration file,
pg_hba.conf. This file is generally found in the path:/etc/postgresql/<version>/main/. -
Add the Hevo IP addresses for your region or
0.0.0.0to allow all IPs to connect:host all user_name 0.0.0.0/0 md5
Create a Database User and Grant Privileges
1. Create a database user (Optional)
Perform the following steps to create a user in your PostgreSQL database:
-
Connect to your PostgreSQL database as an admin user with an SQL client tool, such as psql.
-
Create a database user:
CREATE USER <username> PASSWORD '<password>';Note: Replace the placeholder values in the command above with your own. For example, <username> with hevo.
2. Grant privileges to the user
Grant privileges to the database user connecting to the PostgreSQL database as follows:
-
Connect to your PostgreSQL database instance.
-
(Optional) View existing users and their privileges in your PostgreSQL instance:
psql -U postgres \du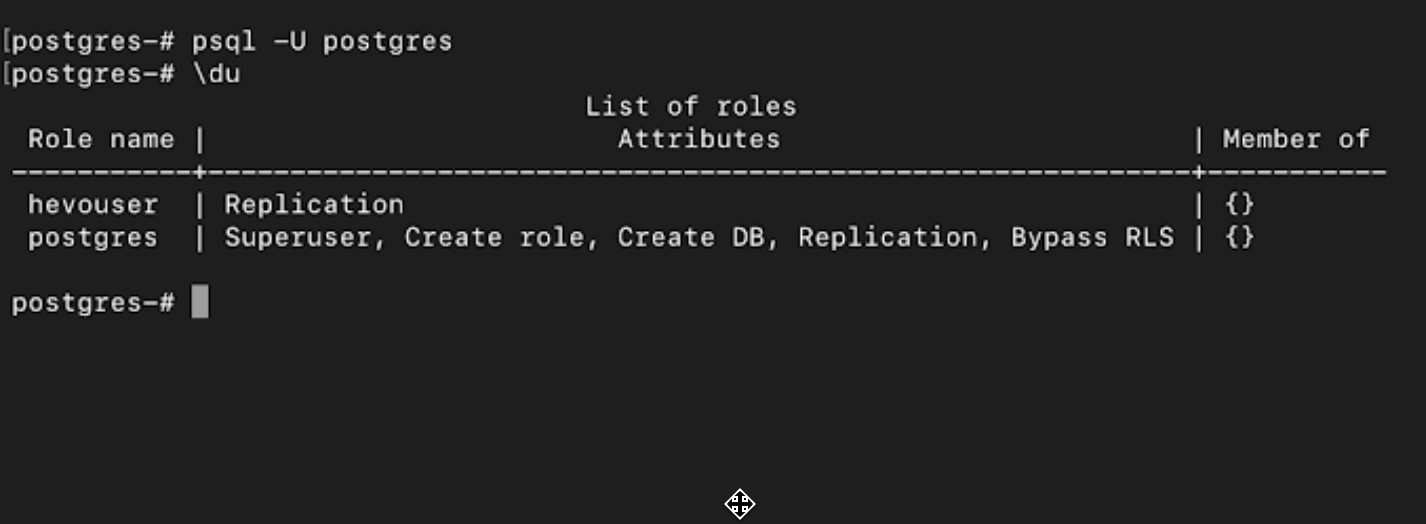
If the privileges are not assigned, perform the next step. Else, proceed to Step 4.
-
Grant the required privileges to the user:
GRANT CONNECT ON DATABASE <database_name> TO <database_username>; GRANT USAGE ON SCHEMA <schema_name> TO <database_username>; -
Alter the schema’s default privileges to grant
SELECTprivileges on tables to the database user:ALTER DEFAULT PRIVILEGES IN SCHEMA <schema_name> GRANT SELECT ON TABLES TO <database_username>;
Specify PostgreSQL Connection Settings
-
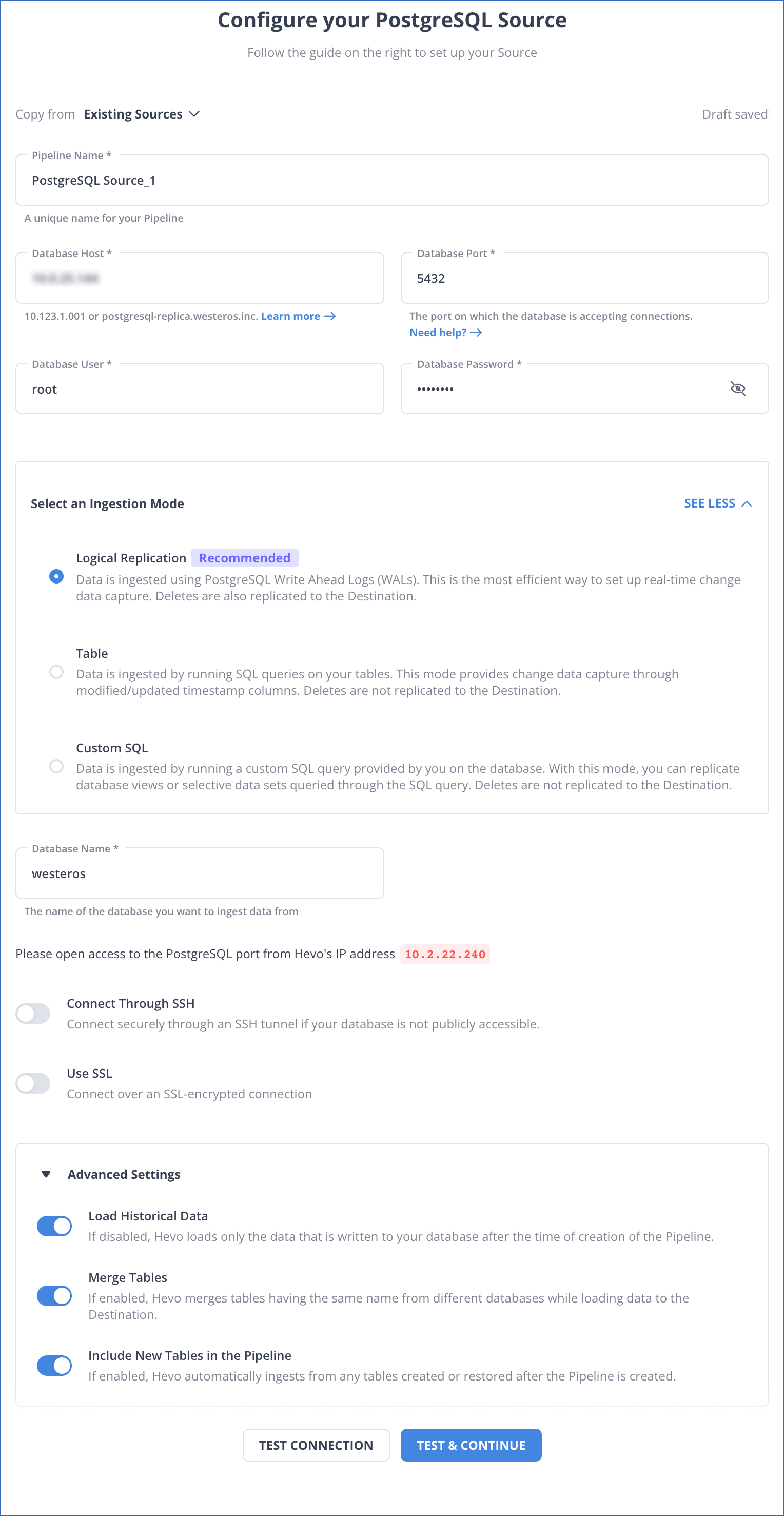
In the Configure your PostgreSQL Source page, specify the following:
-
Pipeline Name: A unique name for your Pipeline, not exceeding 255 characters.
-
Database Host: The PostgreSQL host’s IP address or DNS. For example, 10.123.10.001 or postgresql.westeros.inc.
Note: For URL-based hostnames, exclude the
http://orhttps://part. For example, if the hostname URL is https://postgres.database.westeros.inc, enter postgres.database.westeros.inc. -
Database Port: The port on which your PostgreSQL server listens for connections. Default value: 5432.
-
Database User: The read-only user who has the permission to read tables in your database.
-
Database Password: The password for the read-only user.
-
Select an Ingestion Mode: The desired mode by which you want to ingest data from the Source. This section is expanded by default. However, you can collapse the section by clicking SEE LESS. Default value: Logical Replication.
The available ingestion modes are Logical Replication, Table, and Custom SQL. Additionally, the XMIN ingestion mode is available for Early Access. Logical Replication is the recommended ingestion mode and is selected by default.
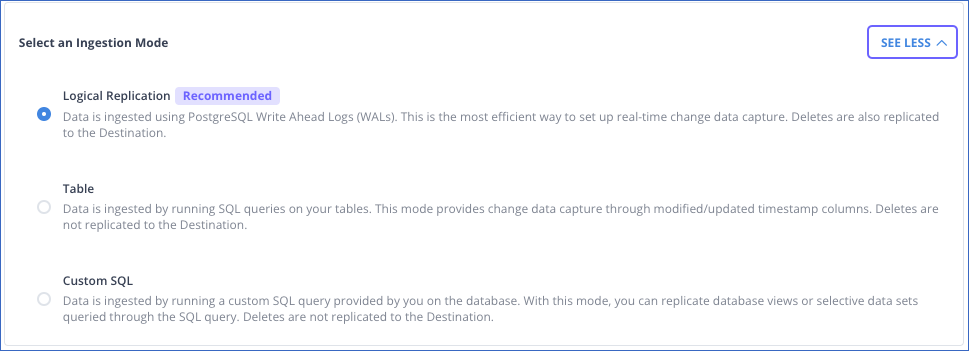
Depending on the ingestion mode you select, you must configure the objects to be replicated. Refer to section, Object and Query Mode Settings for the steps to do this.
Note: For the Custom SQL ingestion mode, all Events loaded to the Destination are billable.
-
Database Name: The name of an existing database that you wish to replicate.
-
Schema Name (Optional): The schema in your database that holds the tables to be replicated. Default value: public.
Note: The Schema Name field is displayed only for Table and Custom SQL ingestion modes.
-
Connection Settings:
-
Connect through SSH: Enable this option to connect to Hevo using an SSH tunnel, instead of directly connecting your PostgreSQL database host to Hevo. This provides an additional level of security to your database by not exposing your PostgreSQL setup to the public. Read Connecting Through SSH.
If this option is turned off, you must whitelist Hevo’s IP addresses.
-
Use SSL: Enable this option to use an SSL-encrypted connection. Specify the following:
-
CA File: The file containing the SSL server certificate authority (CA).
-
Load all CA Certificates: If selected, Hevo loads all CA certificates (up to 50) from the uploaded CA file, else it loads only the first certificate.
Note: Select this check box if you have more than one certificate in your CA file.
-
-
Client Certificate: The client’s public key certificate file.
-
Client Key: The client’s private key file.
-
-
-
Advanced Settings
-
Load Historical Data: Applicable for Pipelines with Logical Replication mode.
If enabled, the entire table data is fetched during the first run of the Pipeline.
If disabled, Hevo loads only the data that was written in your database after the time of creation of the Pipeline. -
Merge Tables: Applicable for Pipelines with Logical Replication mode.
If enabled, Hevo merges tables with the same name from different databases while loading the data to the warehouse. Hevo loads the Database Name field with each record.
If disabled, the database name is prefixed to each table name. Read How does the Merge Tables feature work? -
Include New Tables in the Pipeline: Applicable for all ingestion modes except Custom SQL.
If enabled, Hevo automatically ingests data from tables created in the Source after the Pipeline has been built. These may include completely new tables or previously deleted tables that have been re-created in the Source.
If disabled, new and re-created tables are not ingested automatically. They are added in SKIPPED state in the objects list, in the Pipeline Overview page. You can include these objects post-Pipeline creation to ingest data.You can change this setting later.
-
-
-
Click TEST CONNECTION. This button is enabled once you specify all the mandatory fields. Hevo’s underlying connectivity checker validates the connection settings you provide.
-
Click TEST & CONTINUE to proceed with setting up the Destination. This button is enabled once you specify all the mandatory fields.
Object and Query Mode Settings
Once you have specified the Source connection settings in Step 4 above, do one of the following:
-
For Pipelines configured with the Table or Logical Replication mode:
-
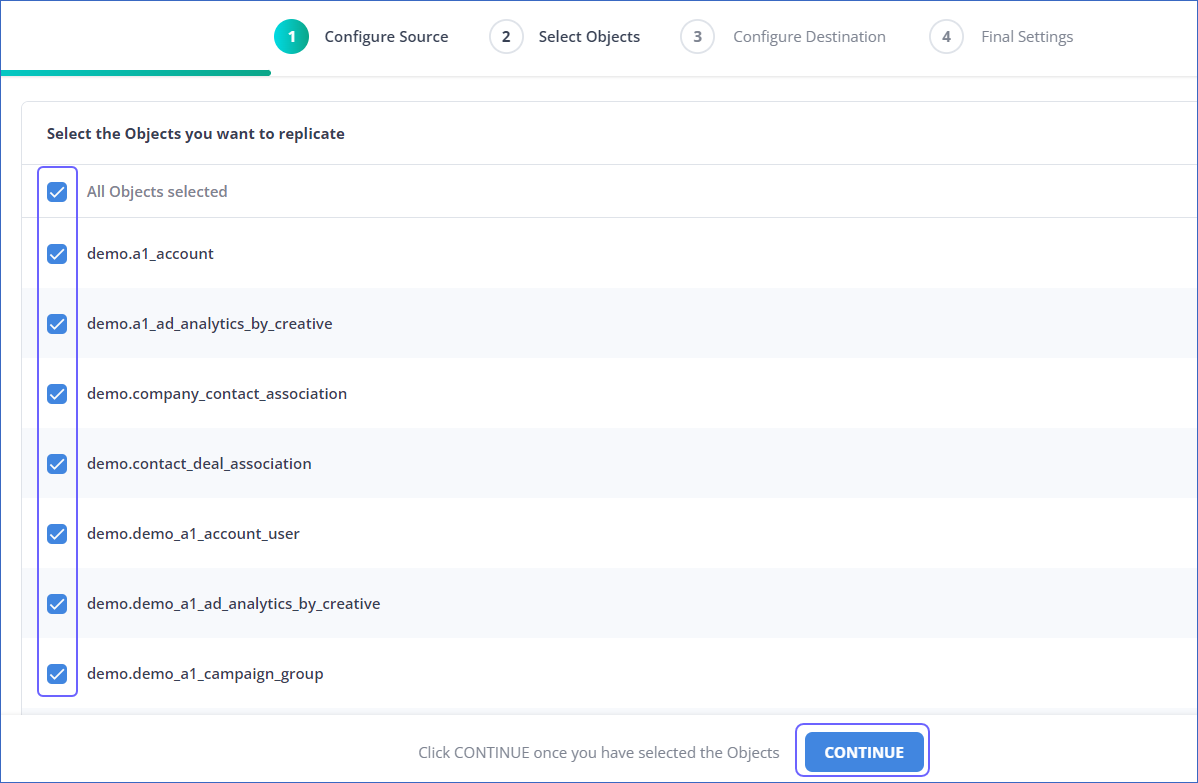
In the Select Objects page, select the objects you want to replicate and click CONTINUE.
Note:
-
Each object represents a table in your database.
-
From Release 2.19 onwards, for log-based Pipelines, you can keep the objects listed in the Select Objects page deselected by default. In this case, when you skip object selection, all objects are skipped for ingestion, and the Pipeline is created in the Active state. You can include the required objects post-Pipeline creation. Contact Hevo Support to enable this option for your teams.
-
-
In the Configure Objects page, specify the query mode you want to use for each selected object.
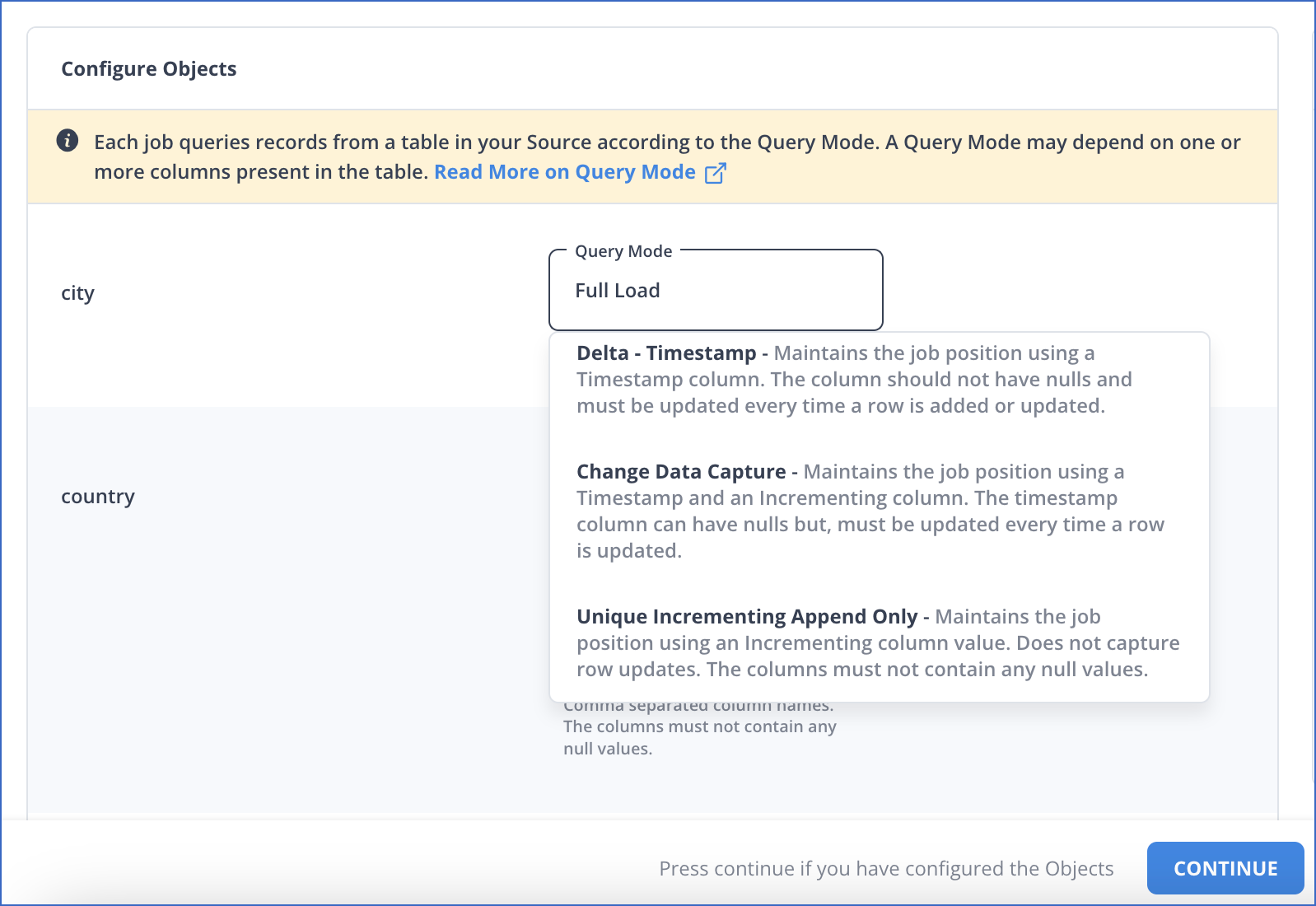
Note: In Full Load mode, Hevo attempts to replicate the full table in a single run of the Pipeline, with an ingestion limit of 25 Million rows.
-
-
For Pipelines configured with the XMIN mode:
-
In the Select Objects page, select the objects you want to replicate.

Note:
-
Each object represents a table in your database.
-
For the selected objects, only new and updated records are ingested using the
XMINcolumn. -
The Edit Config option is unavailable for the objects selected for XMIN-based ingestion. You cannot change the ingestion mode for these objects post-Pipeline creation.
-
-
Click CONTINUE.
-
-
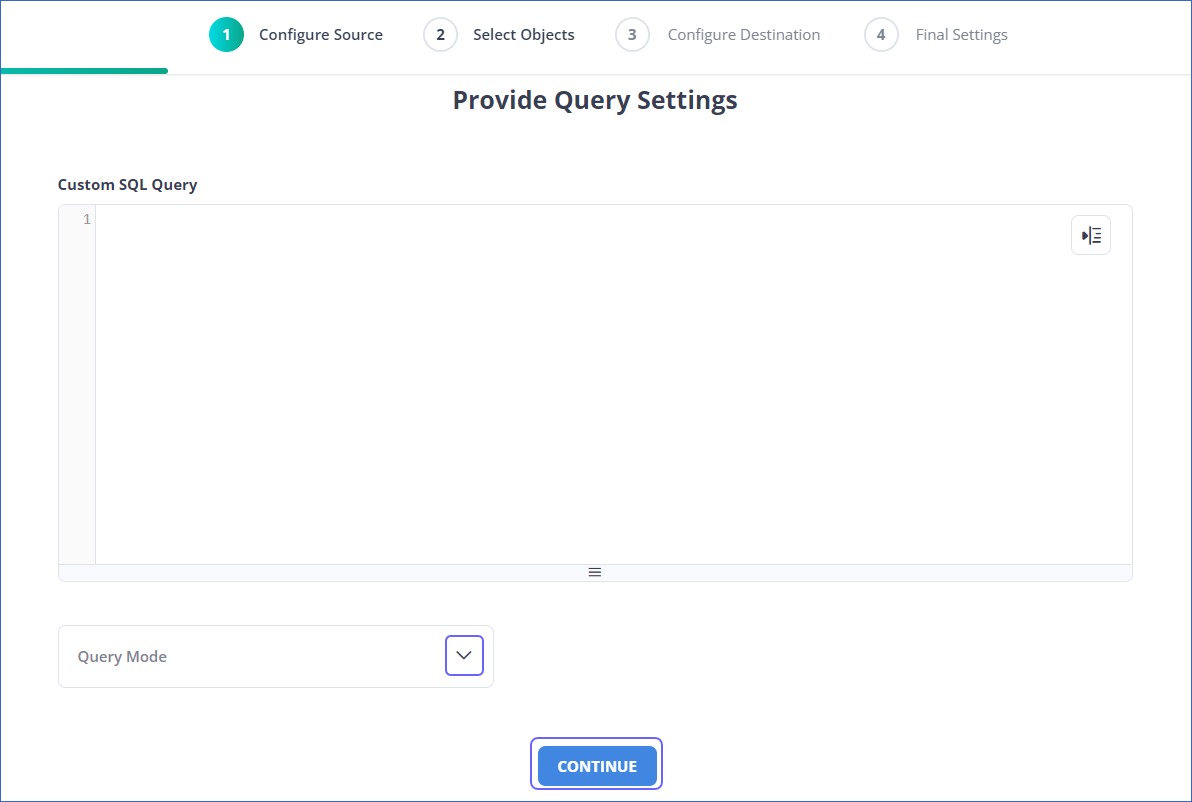
For Pipelines configured with the Custom SQL mode:
-
In the Provide Query Settings page, enter the custom SQL query to fetch data from the Source.
-
In the Query Mode drop-down, select the query mode, and click CONTINUE.
-
Data Replication
| For Teams Created | Ingestion Mode | Default Ingestion Frequency | Minimum Ingestion Frequency | Maximum Ingestion Frequency | Custom Frequency Range (in Hrs) |
|---|---|---|---|---|---|
| Before Release 2.21 | Table | 15 Mins | 15 Mins | 24 Hrs | 1-24 |
| Log-based | 5 Mins | 5 Mins | 1 Hr | NA | |
| After Release 2.21 | Table | 6 Hrs | 30 Mins | 24 Hrs | 1-24 |
| Log-based | 30 Mins | 30 Mins | 24 Hrs | 1-24 |
Note: The custom frequency must be set in hours as an integer value. For example, 1, 2, or 3 but not 1.5 or 1.75.
-
Historical Data: In the first run of the Pipeline, Hevo ingests all available data for the selected objects from your Source database.
-
Incremental Data: Once the historical load is complete, data is ingested as per the ingestion frequency.
Additional Information
Read the detailed Hevo documentation for the following related topics:
Source Considerations
-
If you add a column with a default value to a table in PostgreSQL, entries with it are created in the WAL only for the rows that are added or updated after the column is added. As a result, in the case of log-based Pipelines, Hevo cannot capture the column value for the unchanged rows. To capture those values, you need to:
-
Restart the historical load for the respective object.
-
Run a query in the Destination to add the column and its value to all rows.
-
-
PostgreSQL does not support logical replication on read replicas. To enable log-based replication, you must select the primary database instance.
-
When you delete a row in the Source table, its XMIN value is deleted as well. As a result, for Pipelines created with the XMIN ingestion mode, Hevo cannot track deletes in the Source object(s). To capture deletes, you need to restart the historical load for the respective object.
-
XMIN is a system-generated column in PostgreSQL, and it cannot be indexed. Hence, to identify the updated rows in Pipelines created with the XMIN ingestion mode, Hevo scans the entire table. This action may lead to slower data ingestion and increased processing overheads on your PostgreSQL database host. Due to this, Hevo recommends that you create the Pipeline in the Logical Replication mode.
Note: The XMIN limitations specified above are applicable only to Pipelines created using the XMIN ingestion mode, which is currently available for Early Access.
Limitations
-
The data type Array in the Source is automatically mapped to Varchar at the Destination. No other mapping is currently supported.
-
Hevo does not support data replication from foreign tables, temporary tables, and views.
-
If your Source data has indexes (indices) and constraints, you must recreate them in your Destination table, as Hevo does not replicate them from the Source. It only creates the existing primary keys.
-
Hevo does not set the
__hevo_marked_deletedfield to True for data deleted from the Source table using the TRUNCATE command. This could result in a data mismatch between the Source and Destination tables.
See Also
Revision History
Refer to the following table for the list of key updates made to this page:
| Date | Release | Description of Change |
|---|---|---|
| Mar-18-2024 | 2.21.2 | Updated section, Specify PostgreSQL Connection Settings to add information about the Load all CA certificates option. |
| Mar-05-2024 | 2.21 | Added the Data Replication section. |
| Feb-05-2024 | NA | Updated sections, Specify PostgreSQL Connection Settings and Object and Query Mode Settings to add information about the XMIN ingestion mode. |
| Jan-22-2024 | 2.19.2 | Updated section, Object and Query Mode Settings to add a note about the enhanced object selection flow available for log-based Pipelines. |
| Jan-10-2024 | NA | - Updated section, Source Considerations to add information about limitations of XMIN query mode. - Removed mentions of XMIN as a query mode. |
| Nov-03-2023 | NA | Renamed section, Object Settings to Object and Query Mode Settings. |
| Oct-27-2023 | NA | Added subsection, Create a database user. |
| Oct-03-2023 | NA | Updated sections: - Specify PostgreSQL Connection Settings to describe the schema name displayed in Table and Custom SQL ingestion modes, - Source Considerations to add information about logical replication not supported on read replicas, and - Limitations to add limitations about data replicated by Hevo. |
| Sep-19-2023 | NA | Updated section, Limitations to add information about Hevo not supporting data replication from certain tables. |
| Jun-26-2023 | NA | Added section, Source Considerations. |
| Apr-21-2023 | NA | Updated section, Specify PostgreSQL Connection Settings to add a note to inform users that all loaded Events are billable for Custom SQL mode-based Pipelines. |
| Mar-09-2023 | 2.09 | Updated section, Specify PostgreSQL Connection Settings to mention about SEE MORE in the Select an Ingestion Mode section. |
| Dec-19-2022 | 2.04 | Updated section, Specify PostgreSQL Connection Settings to add information that you must specify all fields to create a Pipeline. |
| Dec-07-2022 | 2.03 | Updated section, Specify PostgreSQL Connection Settings to mention about including skipped objects post-Pipeline creation. |
| Dec-07-2022 | 2.03 | Updated section, Specify PostgreSQL Connection Settings to mention about the connectivity checker. |
| Jan-24-2022 | 1.80 | Removed from Limitations that Hevo does not support UUID datatype as primary key. |
| Dec-20-2021 | 1.78 | Updated section, Update the client authentication file. |
| Sep-09-2021 | 1.71 | Updated the section, Limitations to include information about columns with the UUID data type not being supported as a primary key. |
| Jun-14-2021 | 1.65 | Updated the Grant Privileges to the User section to include latest commands. |